Eagle-eyed users of Android O will have noticed the absence of the 'Allow
unknown sources' setting, which has existed since the earliest days of Android
to facilitate the installation of apps from outside of Google Play and other
preloaded stores. In this post we'll talk about the new Install unknown
apps permission and the security benefits it brings for both Android
users and developers.
Earlier this year we introduced
Protect - comprehensive security services that are always at work to protect
your device from harm. Google Play continues to be one of the safest places for
Android users to download their apps, with the majority of Potentially Harmful
Apps (PHAs) originating from third-party sources.
A common strategy employed by PHA authors is to deliver their apps via a hostile
downloader. For example, a gaming app might not contain malicious code but
instead might notify the user to install a PHA that masquerades as an important
security update. (You can read more about hostile downloaders in the
Security 2016 Year in Review). Users who have enabled the installation of
apps from unknown sources leave themselves vulnerable to this deceptive
behavior.
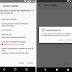
Left (pre-Android O): The install screen for a PHA masquerading as a system
update.
Right (Android O): Before the PHA is installed, the user must first grant
permission to the app that triggered the install.
In Android O, the Install unknown apps permission makes it
safer to install apps from unknown sources. This permission is tied to the app
that prompts the install— just like other runtime permissions—and ensures that
the user grants permission to use the install source before it can prompt the
user to install an app. When used on a device running Android O and higher,
hostile downloaders cannot trick the user into installing an app without having
first been given the go-ahead.
This new permission provides users with transparency, control, and a streamlined
process to enable installs from trusted sources. The Settings app shows the list
of apps that the user has approved for installing unknown apps. Users can
revoke the permission for a particular app at any time.
At any time, users can review the apps that they've allowed for installing
unknown apps. To make the permission-granting process easier, app developers can
choose to direct users to their permission screen as part of the setup
flow.
Developer changes
To take advantage of this new behavior, developers of apps that require the
ability to download and install other apps via the Package Installer may need to
make some changes. If an app uses a targetSdkLevel of 26 or above
and prompts the user to install other apps, the manifest file needs to include
the
permission:
Apps that haven't declared this permission cannot install other apps, a handy
security protection for apps that have no intention of doing so. You can choose
to pre-emptively direct your users to the Install unknown apps
permission screen using the
Intent action. You can also query the state of this permission using the
PackageManager
API.
Remember that
still apply to apps distributed on Google Play if those apps can install and
update other apps. In the majority of cases, such behavior is inappropriate; you
should instead provide a
link to the app's listing on the Play Store.
Be sure to check out the updated
guide that provides more information about installing unknown apps, and stay
tuned for more posts on security hardening in Android O.



.jpg)
0 comments